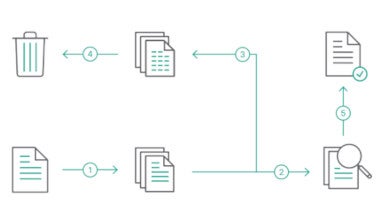
Stop ransomware - without trying to detect it
In these unprecedented times, it’s vital you strengthen your defense with protection that can’t be beaten. Forcepoint’s Security solutions discard ransomware at the boundary and ensure only valid information is delivered.

In these unprecedented times, it’s vital you strengthen your defense with protection that can’t be beaten. Forcepoint’s Security solutions discard ransomware at the boundary and ensure only valid information is delivered.
Cybersecurity for Financial Institutions
Our experts will create a demo focused on the cybersecurity goals of your organization so you can experience the Forcepoint difference firsthand.
Zero false positives
Zero latency
Stop zero-day threats
Pixel-perfect, fully revisable files
Quick & simple installation
Resources
Get the latest from our experts and research partners
Financial Services Security Products